Automating Penetration Tests - Part 2
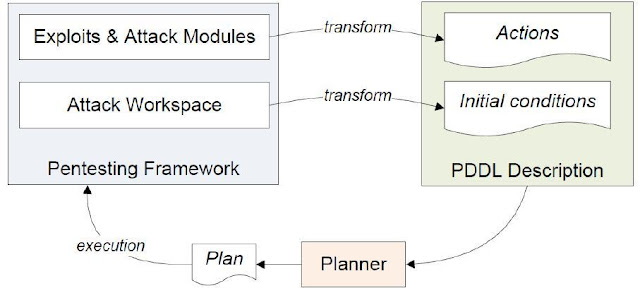
This is part 2 of the article, click here to read part 1 of the article. Modern Approaches to Attack Graphs Generation and Analysis In the modern approach, attack graphs are generated without the full knowledge about the network – which represents real-world scenarios. Then during the attack phase, the rest of the information is learned and the attack graph is altered accordingly. A planner or an intelligent mechanism such as a neural network is used to analyze the graphs and then to generate attacks. There are two notable research papers that discuss on attack planning. Ghosh and Ghosh proposed a new approach to attack planning using a planner [35]. Then Obes et al. have used the same concept and integrated the planner to a penetration testing framework to successfully conduct a penetration test [36].
