Automating Penetration Tests - Part 2
This is part 2 of the article, click here to read part 1 of the article.
Modern Approaches to Attack Graphs Generation and Analysis
In the modern approach, attack graphs are generated without the full knowledge about the network – which represents real-world scenarios. Then during the attack phase, the rest of the information is learned and the attack graph is altered accordingly. A planner or an intelligent mechanism such as a neural network is used to analyze the graphs and then to generate attacks.
There are two notable research papers that discuss on attack planning. Ghosh and Ghosh proposed a new approach to attack planning using a planner [35]. Then Obes et al. have used the same concept and integrated the planner to a penetration testing framework to successfully conduct a penetration test [36].
Figure 3 illustrates the solution proposed by Obes et al. Attack graphs generated from information gathered from the penetration testing framework (initial conditions are results generate by vulnerability scan or a network scan) and it is modeled using a language called Planning Domain Definition Language (PDDL) [37][38]. PDDL is the encoding language that planners understand.
It’s assumed that a vulnerability analysis or a network scan has been conducted prior generation of the initial graph. Researchers have used a transformation algorithm to transform information from the penetration testing domain to the planner’s domain.
There are two main PDDL files that encode information needed. One PDDL file holds encoded details on exploits, exploit’s requirements, exploit results and predicates. Therefore this PDDL file contains all the state transition operators (actions). In a second PDDL file contains encoded information obtained from the initial vulnerability scan (initial conditions) and goals of the penetration test. This includes networks, hosts, operating systems versions, services running, open ports, etc.
From the PDDLs, the planner generates a plan – which is a series of actions in the planner’s domain. Figure 4 shows a list of actions generated by the planner. This plan is transformed into penetration testing frameworks domain and then executed in the framework. Results are returned back to the planner through the transformation algorithm as updates in PDDL files. This cycle goes on until a goal is reached.
Planners
A variant of Planner called GraphPlan is a search algorithm which searches for a solution within a large state space. GraphPlan takes Output from the vulnerability scan on the network configuration, the attacker's goal, and exploits as input [35]. Both Obes’ [36] and Ghosh’s [35] researches have used the same planner: SGPlan [39][39].
Correlate Vulnerabilities for Attack Planning
Computer networks interconnect many different devices so that they can interact with each other. As these interconnections occur, weaknesses on one application can affect others that they interact with. For an example if a web server and an FTP server are hosted on the same host and if the attacker can upload executable files via the FTP service and get them executed via the web service, then there’s vulnerability exists in the system.
In isolation, vulnerability might have a medium or low impact, but when they are combined, the impact can be critical. To identify such scenarios, the vulnerability correlation is important. Figure 5 depicts the vulnerability correlation method proposed by X. Liu et al and the researchers have used transition rules to perform vulnerability correlation based on the fact base [40].
Fact base consists of a number of facts. A fact is an information about a particular host on the system. The definition of a fact is given as "... a triple (h, v, n), where (1) h is a set of attribute names about host configuration, each with an associated domain of values, (2) v is a list of vulnerability information about h, (3) n is an array of connection matrix used to identify all of the connection relations connected to h."[40]. Transition rules define logical relationships among facts. Then a correlation algorithm uses facts and transition rules to generate an attack graph.
However, the researchers have not produced any automated mechanism to identify transition rules. But having a systematic mechanism to identify interaction among entities and correlate vulnerabilities and identify potential attack vectors is very important to automate a penetration test.
Post-Exploitation
Once an exploit is successful the penetration tester gets access to the exploited system. The type of access (remote shell, admin page of a web site) and the privilege level depends on the target and the application. With the post-exploitation steps, the pentester check what type of information can he gather from the target, what types of attack can be launched using the compromised target, etc. [41].
Information Gathering
Information gathering is the first step that the penetration tester performs after successful exploitation. He checks what types of privileges (root, non-root) does he have. Information about the IP addresses, operating systems, users on the system, operating system and patch levels are gathered [41]. This information is vital not only when measuring the risk and the impact of the vulnerability, but also can be used in next exploits.
Pivoting
A successful exploit gives the pentester access to the target host, but because most of the networks are segmented, he does not have access to another resource on the target system. Pivoting is a process which allows the pentester reach systems that were not visible or accessible to him before, by routing his traffic through the compromised host [42]. The compromised host is used as a launch pad for the other attacks. The penetration tester can also exploit the trust relationships of the compromised host.
Privilege Escalation
Applications run under various privileges of when they are exploited, the pentester get generally the same privilege as the application. However, it’s necessary to check if there are ways to escalate privileges locally. With higher privileges, the pentester can gather more information and perform more tasks using the compromised host [43].
Meterpreter
Meterpreter is an advanced payload that is included in the Metasploit penetration testing framework. Meterpreter is often used for post exploitation because it provides simplified access to the remote system. It allows developers to write their own extensions in the form of shared object (DLL) files that can be uploaded and injected into a running process on a target computer after exploitation has occurred. Meterpreter and its extensions are executed entirely from memory and never write them self to the disk. This allows them to execute stealthily standard Anti-Virus detection [44].
Post Exploitation Automation
Irani and Weippl proposed a mechanism to automate post exploitation steps using the scripting language that is provided by Meterpreter’s API [42]. This Meterpreter script can be executed either directly in a Meterpreter session or can be called as a batch process once the Meterpreter is spawned. In order to fully automate post exploitation steps, the latter option can be used.
References
[35] N. Ghosh and S.K. Ghosh, “An intelligent technique for generating minimal attack graph,” First Workshop on Intelligent Security (Security and Artificial Intelligence), 2009.
[36] J.L. Obes, C. Sarraute, and G. Richarte, “Attack Planning in the Real World,” Working Notes for the 2010 AAAI Workshop on Intelligent Security (SecArt), 2010, p. 10.
[37] H.L. Younes and M.L. Littman, “PPDDL1. 0: An extension to PDDL for expressing planning domains with probabilistic effects,” In Proceedings of the 14th International Conference on Automated Planning and Scheduling, 2003.
[38] S. Edelkamp and J. Hoffmann, “PDDL2. 2: The language for the classical part of the 4th international planning competition,” 4th International Planning Competition (IPC’04), at ICAPS’04, 2004.
[39] Y. Chen, C.W. Hsu, and B.W. Wah, “SGPlan: Subgoal partitioning and resolution in planning,” Edelkamp et al. (Edelkamp, Hoffmann, Littman, & Younes, 2004), 2004.
[40] X. Liu, D. Xiao, N. Ma, and J. Yu, “A Scalable, Vulnerability Modeling and Correlating Method for Network Security,” Scalable Information Systems, 2009, pp. 217–227.
[41] D. Maynor and K.K. Mookhey, Metasploit toolkit for penetration testing, exploit development, and vulnerability research, Syngress Media Inc, 2007.
[42] M.T. Irani and E.R. Weippl, “Automation of post-exploitation,” Security Technology, 2009, pp. 250–257.
[43] Z. Fang-fang, C. Xiu-zhen, and L.I. Jian-hua, “Generation Method of Network Attack Graphs Based on Privilege Escalation [J],” Computer Engineering, vol. 34, 2008, pp. 158–160.
[44] M. Miller, Metasploit's meterpreter, December, 2004.
[45] Y.Z. Zhang, X.C. Yun, B.X. Fang, and T. Zhang, “A mining method for computer vulnerability correlation,” International Journal of Innovative Computing, Information, and Control, vol. 1, 2005, pp. 43–51.
Modern Approaches to Attack Graphs Generation and Analysis
In the modern approach, attack graphs are generated without the full knowledge about the network – which represents real-world scenarios. Then during the attack phase, the rest of the information is learned and the attack graph is altered accordingly. A planner or an intelligent mechanism such as a neural network is used to analyze the graphs and then to generate attacks.
There are two notable research papers that discuss on attack planning. Ghosh and Ghosh proposed a new approach to attack planning using a planner [35]. Then Obes et al. have used the same concept and integrated the planner to a penetration testing framework to successfully conduct a penetration test [36].
Figure 3 illustrates the solution proposed by Obes et al. Attack graphs generated from information gathered from the penetration testing framework (initial conditions are results generate by vulnerability scan or a network scan) and it is modeled using a language called Planning Domain Definition Language (PDDL) [37][38]. PDDL is the encoding language that planners understand.
It’s assumed that a vulnerability analysis or a network scan has been conducted prior generation of the initial graph. Researchers have used a transformation algorithm to transform information from the penetration testing domain to the planner’s domain.
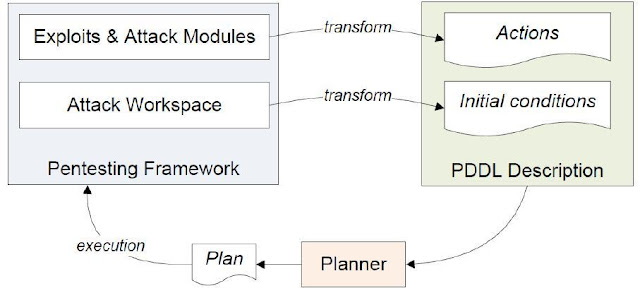 |
| Figure 3: Architecture of the system proposed by Obes et al.[36] |
There are two main PDDL files that encode information needed. One PDDL file holds encoded details on exploits, exploit’s requirements, exploit results and predicates. Therefore this PDDL file contains all the state transition operators (actions). In a second PDDL file contains encoded information obtained from the initial vulnerability scan (initial conditions) and goals of the penetration test. This includes networks, hosts, operating systems versions, services running, open ports, etc.
From the PDDLs, the planner generates a plan – which is a series of actions in the planner’s domain. Figure 4 shows a list of actions generated by the planner. This plan is transformed into penetration testing frameworks domain and then executed in the framework. Results are returned back to the planner through the transformation algorithm as updates in PDDL files. This cycle goes on until a goal is reached.
Planners
A variant of Planner called GraphPlan is a search algorithm which searches for a solution within a large state space. GraphPlan takes Output from the vulnerability scan on the network configuration, the attacker's goal, and exploits as input [35]. Both Obes’ [36] and Ghosh’s [35] researches have used the same planner: SGPlan [39][39].
 |
| Figure 4: Series of actions generated by the planner [36] |
Correlate Vulnerabilities for Attack Planning
Computer networks interconnect many different devices so that they can interact with each other. As these interconnections occur, weaknesses on one application can affect others that they interact with. For an example if a web server and an FTP server are hosted on the same host and if the attacker can upload executable files via the FTP service and get them executed via the web service, then there’s vulnerability exists in the system.
In isolation, vulnerability might have a medium or low impact, but when they are combined, the impact can be critical. To identify such scenarios, the vulnerability correlation is important. Figure 5 depicts the vulnerability correlation method proposed by X. Liu et al and the researchers have used transition rules to perform vulnerability correlation based on the fact base [40].
 |
| Figure 5: Network assessment method proposed by X. Liu et al. [40] using vulnerability correlation |
Fact base consists of a number of facts. A fact is an information about a particular host on the system. The definition of a fact is given as "... a triple (h, v, n), where (1) h is a set of attribute names about host configuration, each with an associated domain of values, (2) v is a list of vulnerability information about h, (3) n is an array of connection matrix used to identify all of the connection relations connected to h."[40]. Transition rules define logical relationships among facts. Then a correlation algorithm uses facts and transition rules to generate an attack graph.
However, the researchers have not produced any automated mechanism to identify transition rules. But having a systematic mechanism to identify interaction among entities and correlate vulnerabilities and identify potential attack vectors is very important to automate a penetration test.
Post-Exploitation
Once an exploit is successful the penetration tester gets access to the exploited system. The type of access (remote shell, admin page of a web site) and the privilege level depends on the target and the application. With the post-exploitation steps, the pentester check what type of information can he gather from the target, what types of attack can be launched using the compromised target, etc. [41].
Information Gathering
Information gathering is the first step that the penetration tester performs after successful exploitation. He checks what types of privileges (root, non-root) does he have. Information about the IP addresses, operating systems, users on the system, operating system and patch levels are gathered [41]. This information is vital not only when measuring the risk and the impact of the vulnerability, but also can be used in next exploits.
Pivoting
A successful exploit gives the pentester access to the target host, but because most of the networks are segmented, he does not have access to another resource on the target system. Pivoting is a process which allows the pentester reach systems that were not visible or accessible to him before, by routing his traffic through the compromised host [42]. The compromised host is used as a launch pad for the other attacks. The penetration tester can also exploit the trust relationships of the compromised host.
Privilege Escalation
Applications run under various privileges of when they are exploited, the pentester get generally the same privilege as the application. However, it’s necessary to check if there are ways to escalate privileges locally. With higher privileges, the pentester can gather more information and perform more tasks using the compromised host [43].
Meterpreter
Meterpreter is an advanced payload that is included in the Metasploit penetration testing framework. Meterpreter is often used for post exploitation because it provides simplified access to the remote system. It allows developers to write their own extensions in the form of shared object (DLL) files that can be uploaded and injected into a running process on a target computer after exploitation has occurred. Meterpreter and its extensions are executed entirely from memory and never write them self to the disk. This allows them to execute stealthily standard Anti-Virus detection [44].
Post Exploitation Automation
Irani and Weippl proposed a mechanism to automate post exploitation steps using the scripting language that is provided by Meterpreter’s API [42]. This Meterpreter script can be executed either directly in a Meterpreter session or can be called as a batch process once the Meterpreter is spawned. In order to fully automate post exploitation steps, the latter option can be used.
References
[35] N. Ghosh and S.K. Ghosh, “An intelligent technique for generating minimal attack graph,” First Workshop on Intelligent Security (Security and Artificial Intelligence), 2009.
[36] J.L. Obes, C. Sarraute, and G. Richarte, “Attack Planning in the Real World,” Working Notes for the 2010 AAAI Workshop on Intelligent Security (SecArt), 2010, p. 10.
[37] H.L. Younes and M.L. Littman, “PPDDL1. 0: An extension to PDDL for expressing planning domains with probabilistic effects,” In Proceedings of the 14th International Conference on Automated Planning and Scheduling, 2003.
[38] S. Edelkamp and J. Hoffmann, “PDDL2. 2: The language for the classical part of the 4th international planning competition,” 4th International Planning Competition (IPC’04), at ICAPS’04, 2004.
[39] Y. Chen, C.W. Hsu, and B.W. Wah, “SGPlan: Subgoal partitioning and resolution in planning,” Edelkamp et al. (Edelkamp, Hoffmann, Littman, & Younes, 2004), 2004.
[40] X. Liu, D. Xiao, N. Ma, and J. Yu, “A Scalable, Vulnerability Modeling and Correlating Method for Network Security,” Scalable Information Systems, 2009, pp. 217–227.
[41] D. Maynor and K.K. Mookhey, Metasploit toolkit for penetration testing, exploit development, and vulnerability research, Syngress Media Inc, 2007.
[42] M.T. Irani and E.R. Weippl, “Automation of post-exploitation,” Security Technology, 2009, pp. 250–257.
[43] Z. Fang-fang, C. Xiu-zhen, and L.I. Jian-hua, “Generation Method of Network Attack Graphs Based on Privilege Escalation [J],” Computer Engineering, vol. 34, 2008, pp. 158–160.
[44] M. Miller, Metasploit's meterpreter, December, 2004.
[45] Y.Z. Zhang, X.C. Yun, B.X. Fang, and T. Zhang, “A mining method for computer vulnerability correlation,” International Journal of Innovative Computing, Information, and Control, vol. 1, 2005, pp. 43–51.

Comments
Post a Comment
Please note that comments are moderated in order to stop comment spam. Comments with unwanted links (those who are trying to use blackhat SEO) are reported as spam.