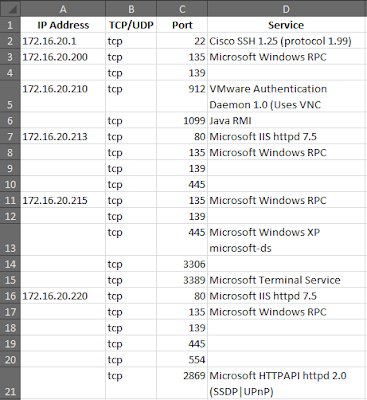
Configure Policy-Based Routing On Check Point Secure Platform

There's no straight-forward way to achieve policy-based routing on Check Point SPLAT (Secure Platform). Since SPLAT is Linux-based and Check Point firewalls relies on operating system routing functions, policy-based routing is also archived through iproute2 - a set of utilities used to control network traffic on Linux systems. iproute2 is available with most of the Linux distributions (including SPLAT) with a kernel version above 2.2. For more information about iproute2, please refer to the links in the Additional References section of this article. When configuring policy-based routing with iproute2 on SPLAT, there is some important point you need to remember. You need to configure a routing table per policy and it's independent of your normal routing table Because of that, once a policy is matched only that particular table is looked for routing Therefore you must manually add all the routing information (including directly connected routes) for each and every table y...